Hackers Are Logging In – Not Breaking In
What if the greatest threat to your business wasn’t a fortress being stormed—but an invited guest using your own key?
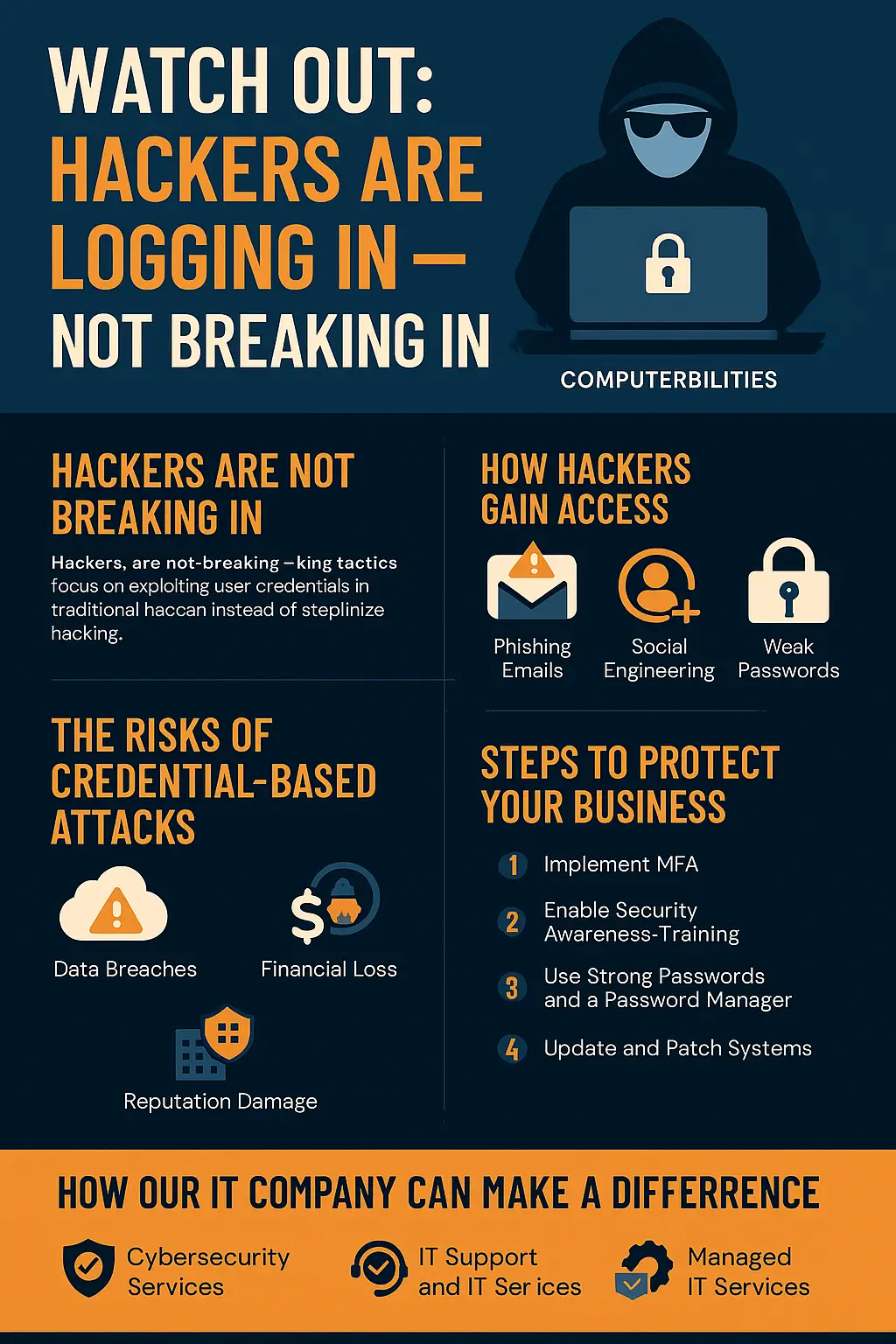
That’s right. Watch Out Hackers Are Logging In – Not Breaking In paints a stark reality: cybercriminals aren’t smashing walls—they’re simply walking in with your credentials. And chances are, you’re unknowingly handing them the keys.
The New Front Door – Identity-Based Attacks Are on the Rise
- What’s changing? Research shows that in 2024, over 67% of serious security breaches stemmed from stolen logins.
- High‑profile failure isn’t only for giants. Brands like MGM and Caesars were compromised this way—and if they’re vulnerable, so are small‑to‑mid‑sized businesses like yours.
How Hackers Are “Logging In”
The shift from brute force to deception:
- Phishing & spoofed login pages—the baited traps that lured unsuspecting employees to enter credentials.
- SIM‑swapping to intercept SMS‑based 2FA codes.
- MFA fatigue attacks—flooding users with push notifications until one gets accepted in error.
- Third‑party and personal device exposures—attackers exploit vendor help desks, remote workers, and peripheral logins.
- Help desk social engineering, such as through Teams chats to reset credentials or bypass MFA entirely.
Why Traditional IT Security Isn’t Enough
- Outdated mindset: Many still assume hackers must “break in” through firewalls—when in reality, stolen credentials are the easiest entry point.
- Credential stuffing & password reuse: Stolen passwords get recycled across platforms; even a 0.1% success rate on millions of attempts can devastate accounts.
- Supply‑chain identity breaches: The Okta incident (and others like Snowflake) show that attacks on identity providers ripple to clients—identity is now the core battleground.
Your Real‑World Risk—Small Business + Managed IT
Whether you’re a boutique firm in Raleigh or a clinic in Durham, hackers don’t need to compromise code—they just need valid credentials. As one article puts it:
“Attackers don’t hack in; they log in.”
—Hayden Evans, ReliaQuest analyst
That makes every login prompt, every helpdesk call, and every MFA request a possible attack vector—especially if your IT support or managed IT services don’t actively defend against these new tactics.
Defense Blueprint – Stop Hackers at Login
- Enable robust, phishing‑resistant MFA
- Use app‑based or hardware security keys—not SMS texts.
- Employee cybersecurity training
- Educate on spotting fake emails, popups, MFA overload—and how to flag or escalate suspicions.
- Principle of least privilege
- Use role‑based access to limit the damage a compromised account can caus.
- Adopt passwordless methods or strong password hygiene
- Encourage password managers, passkeys, security keys, or biometric logins.
- Harden help desk and third‑party protocols
- Enforce strict verification before resetting credentials or granting access—especially over remote links.
- Continuous monitoring and zero‑trust
- Deploy behavioral analytics, unusual-login detection, zero standing privilege, and just‑in‑time access adjustments.
Why “Logging In” Demands Better IT Services
Compared to traditional “break‑in” prevention, identity‑driven tactics require ongoing vigilance across access, training, and monitoring. That’s where modern IT support and managed IT services shine:
- Cybersecurity services integrated into daily operations
- Proactive IT support that enforces MFA, audits permissions, and guides secure behavior
- Efficient IT company‑led implementation—balancing protection without disrupting productivity
How Computerbilities Makes the Difference
At Computerbilities, we understand that hackers are logging in—not breaking in. Our North Carolina‑based team offers:
- Comprehensive cybersecurity services, including phishing‑resistant MFA, behavior‑based monitoring, and zero‑trust frameworks
- Seasoned IT support that trains your team, enforces secure login practices, and audits access
- Scalable managed IT services that protect your systems without slowing your people
- A local IT company with deep roots in NC business culture—your trusted partner in defense
Don’t wait for an identity‑based breach to happen. Partner with Computerbilities today and let us help you lock out unauthorized logins while keeping your team running.

