Cyber Threat Information-Sharing Slows as Liability Concerns Rise
How Legal Uncertainty Threatens Cybersecurity Collaboration Across North Carolina and Beyond
Introduction: A Silent Setback in the Fight Against Cyber Threats
In the ever-evolving landscape of cybersecurity, information is the most powerful weapon. The ability of organizations, governments, and security experts to share cyber threat intelligence—malware signatures, phishing patterns, IP addresses, or indicators of compromise—has saved countless businesses from catastrophic breaches.
But what happens when that flow of information slows to a trickle?
That’s exactly what the United States faces today. The expiration of the Cybersecurity Information Sharing Act (CISA) of 2015, coupled with rising liability fears among private companies, has triggered a chilling effect. Across states including North Carolina, organizations are growing wary of sharing sensitive data about cyber incidents, fearing potential lawsuits, regulatory scrutiny, or reputational damage.
As a result, a once-vital collaboration framework—meant to keep the nation safer from cyber threats—is now being stifled by legal ambiguity. This blog unpacks how we got here, why it matters, and what can be done to rebuild trust and momentum in cybersecurity information sharing.
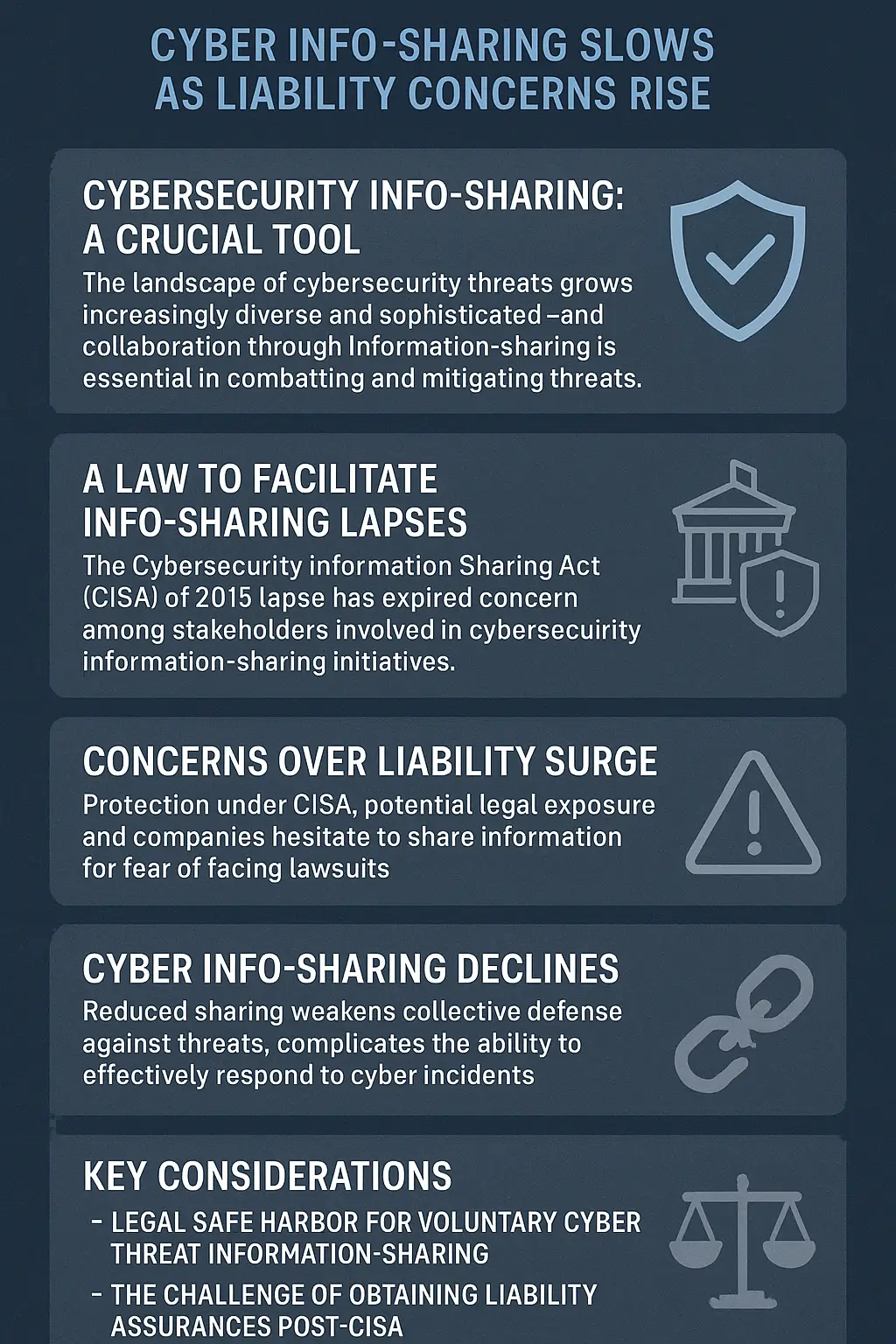
The Foundations — What the Cybersecurity Information Sharing Act (CISA) Meant
Back in 2015, when cyber threats like ransomware and nation-state espionage were intensifying, Congress passed the Cybersecurity Information Sharing Act (CISA). Its goal was straightforward but ambitious:
- Encourage private companies and government entities to share information about cyber threats.
- Protect organizations from liability when they shared this information in good faith.
- Strengthen public-private cooperation, particularly between critical infrastructure sectors and the Department of Homeland Security (DHS).
The law created a bridge between public and private entities—think of it as a “cyber neighborhood watch.” If one company spotted suspicious digital activity, others could be alerted before damage spread.
However, with the law’s expiration in late 2025, the legal protections that once underpinned that cooperation have vanished.
The Expiration Heard Around the Cyber World
The expiration of CISA 2015 couldn’t have come at a worse time. The federal government was grappling with a partial shutdown, diverting attention and resources from cybersecurity policy. According to reporting from The Hill and CSO Online, the lapse has created confusion across industries about what can—and cannot—be safely shared with federal agencies.
Without clear liability protections, many firms have paused or reduced their cyber info-sharing activities, fearing lawsuits under privacy or consumer protection laws.
As Imprivata and Mayer Brown note, this regulatory limbo means that:
- Companies risk exposing themselves to legal claims if data is misused or mishandled.
- There’s no guarantee that shared threat information won’t later be subpoenaed or leaked.
- The absence of unified federal guidance leaves cybersecurity teams unsure whether cooperation is worth the risk.
This hesitation is being felt across sectors—from banking and healthcare to manufacturing and local government.
Why Information Sharing Matters More Than Ever
Cybersecurity has always been a team sport. When information sharing breaks down, the entire defensive line weakens.
- Faster Detection and Response
Shared intelligence enables organizations to recognize patterns early. For example, if a North Carolina hospital detects a phishing campaign, that data can help other hospitals or insurance providers block similar attacks.
- Reduced Duplication of Effort
When every IT team works in isolation, they reinvent the wheel with each incident. Collaborative cyber info-sharing eliminates redundancy, helping businesses pool insights and focus on higher-order threats.
- National Security Implications
In sectors like defense, energy, or transportation, delayed communication can have devastating consequences. As seen in the Colonial Pipeline attack, one incident can ripple across the national economy in hours.
- Cost and Insurance Impacts
Cyber insurance providers are now assessing higher risk premiums for organizations not participating in shared intelligence frameworks. In short, isolation costs money.
Why Companies Are Pulling Back — The Rise of Liability Anxiety
So why has information-sharing slowed so dramatically? Three intertwined forces are at play:
- Legal Uncertainty
The expiration of CISA 2015 stripped away key liability protections. Without them, even well-intentioned data sharing can lead to lawsuits if personal or customer data is inadvertently exposed.
- Reputational Risk
No company wants to be the headline: “Local Firm Shares Threat Data — Accidentally Exposes Customer Info.” The fear of media backlash often outweighs the perceived security benefit.
- Lack of Trust in Federal Systems
Some private sector leaders worry about how the government might use or store the data they share. With breaches affecting even federal systems, skepticism has grown.
In a LinkedIn analysis by cybersecurity attorney Duane Pozza, experts argue that “legal friction, not technical limitations, has become the biggest barrier to cyber collaboration.”
The North Carolina Perspective — Local Risks and Readiness
North Carolina’s economy runs on a diverse digital backbone: financial firms in Charlotte, biotech startups in the Research Triangle, universities handling sensitive research data, and manufacturers leveraging smart factories.
That means the state is particularly vulnerable when cyber threat information sharing slows.
- Higher Risk for SMBs
Small and mid-sized businesses (SMBs) make up 99% of North Carolina’s enterprises. Without shared intel from larger firms, these smaller players lose critical early warnings.
- Healthcare and Education at Risk
Hospitals, universities, and local government agencies often rely on Managed IT Services for protection. These providers depend on shared threat feeds—when those go dark, detection time skyrockets.
- Municipal Vulnerabilities
Cities like Raleigh and Durham have invested heavily in smart infrastructure. But as these systems grow, so does their exposure. Without strong information-sharing networks, municipalities risk being caught off guard by ransomware or supply-chain attacks.
In essence, when Washington slows, North Carolina feels it first.
Industry Voices — A Call for Revival
Cybersecurity leaders across the country are sounding the alarm. According to Imprivata’s press release, CEOs and CISOs from major healthcare and tech firms are urging Congress to reinstate the CISA framework with modernized safeguards.
Meanwhile, Senator Gary Peters has proposed a bill to revive and update the law, adding retroactive liability protections for companies that shared data after its lapse.
Legal experts from Mayer Brown highlight that unless Congress acts swiftly, the chilling effect could take years to reverse.
Industry groups such as the Cybersecurity Coalition and U.S. Chamber of Commerce are lobbying for a permanent solution that balances privacy with protection.
The Bigger Picture — A Global Challenge
The slowdown in U.S. cyber info-sharing mirrors similar patterns abroad. The EU’s GDPR, while crucial for privacy, has also limited data exchange between European firms. In Asia, nations like Japan and Singapore are establishing bilateral agreements to overcome legal roadblocks.
This global fragmentation highlights the tension between data protection and national defense. In the digital age, walls built to protect privacy can inadvertently blind us to shared threats.
Real-World Consequences — When Silence Becomes a Threat
Imagine two companies—one in Charlotte and another in Texas—both using the same cloud provider.
The Texas firm detects unusual traffic from a known malicious IP but keeps it in-house due to liability concerns. Days later, the same attacker exploits the same vulnerability in the Charlotte firm’s system, stealing sensitive data and crippling operations.
This isn’t hypothetical. Cybersecurity researchers warn that delayed sharing can multiply attack impact tenfold.
The 2021 SolarWinds breach is a prime example: threat data wasn’t circulated quickly enough, allowing the attackers to stay hidden for months. The lesson is clear—silence isn’t safety; it’s surrender.
Restoring Confidence — What Businesses Can Do Now
Even without federal clarity, organizations can take proactive steps to maintain secure and compliant information sharing:
- Join Trusted ISACs and ISAOs
Information Sharing and Analysis Centers (ISACs) like MS-ISAC or H-ISAC remain vital networks where vetted members share sanitized threat data.
- Adopt Zero-Trust Frameworks
By minimizing internal risk exposure, businesses can share only necessary data without revealing sensitive infrastructure details.
- Work Through Managed IT Service Providers
In North Carolina, partnering with local Managed IT Services firms offers dual benefits: compliance expertise and secure data exchange channels.
- Establish Internal Sharing Policies
Define what data can be shared, how it must be anonymized, and who approves releases. A formal process builds confidence.
- Monitor Legislative Developments
The revival of the CISA framework may include retroactive protections. Staying informed will help businesses resume participation quickly.
Looking Ahead — Policy, Trust, and Technology
To restore a healthy cyber ecosystem, both policymakers and industry leaders must act decisively.
- Legislative Reform
Congress must re-enact a modernized version of the CISA law that balances liability protection with accountability.
- Public-Private Collaboration 2.0
Beyond compliance, we need trust-based partnerships. Local governments in North Carolina could model new frameworks that demonstrate effective collaboration.
- AI and Automation in Threat Sharing
Machine learning can anonymize and distribute threat intel without exposing private data—solving part of the liability puzzle.
- A Culture of Collective Defense
Just as communities unite against physical disasters, the digital world needs a mindset shift. Collaboration must be the default, not the exception.
Silence Is the New Vulnerability
The expiration of the Cybersecurity Information Sharing Act has cast a long shadow over America’s digital defenses. But the real danger isn’t the lack of a law—it’s the fear that stops good actors from speaking up.
For North Carolina’s businesses, universities, and local governments, the path forward is clear: embrace collaboration, advocate for reform, and prepare internally. Cyber threats won’t wait for Washington to act.
In cybersecurity, every second counts—and every shared insight could save thousands from the next breach.

