NASCAR Data Breach via Medusa Ransomware: A Wake-Up Call for North Carolina Businesses
In the world of business, few things are as devastating as a loss of trust. Customers and clients trust you to protect their information, keep transactions secure, and ensure business continuity. But what happens when even iconic brands—like NASCAR—fall victim to cybercriminals?
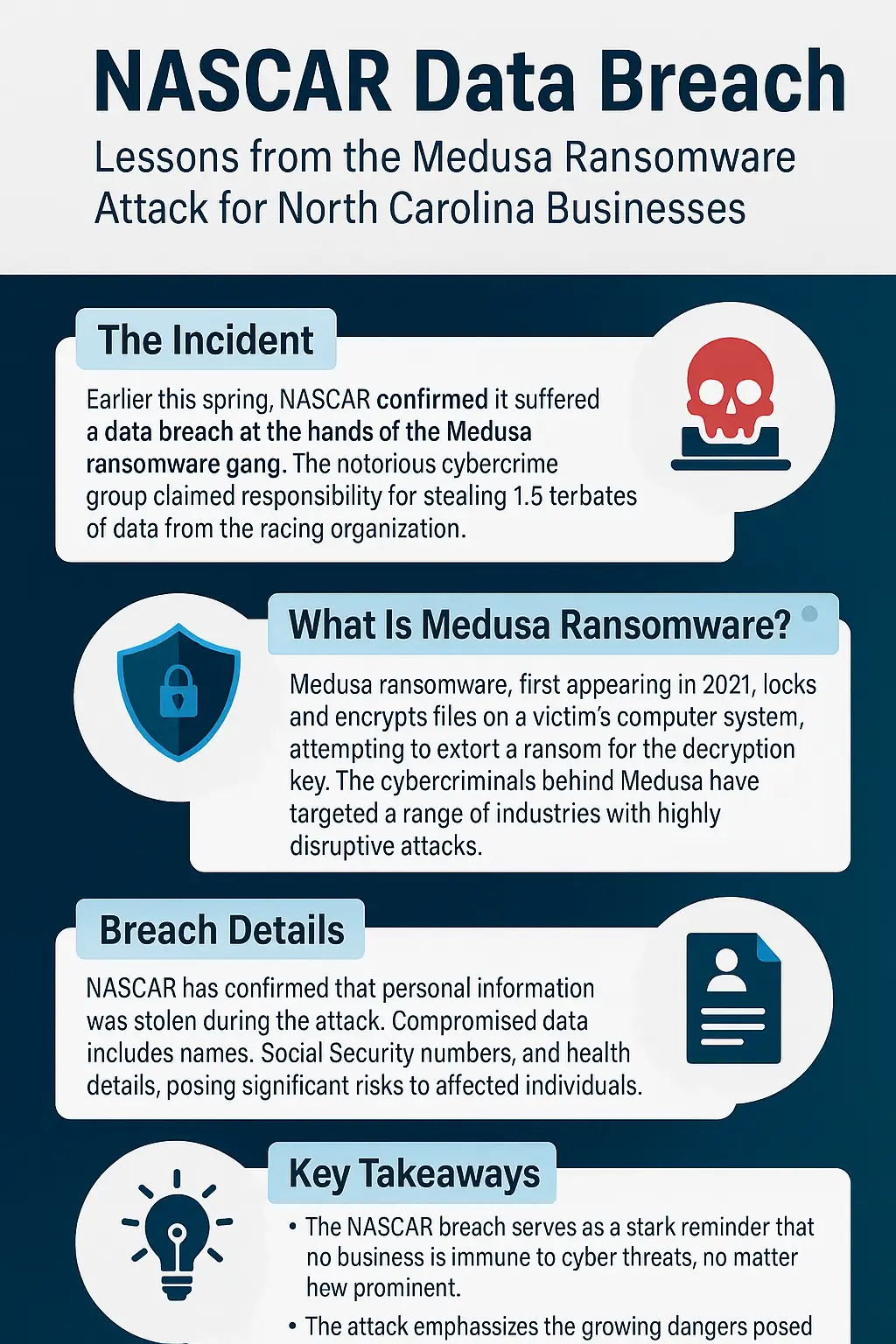
In early 2025, NASCAR confirmed a data breach tied to the Medusa ransomware group, one of the most aggressive cybercriminal syndicates operating today. The incident involved the theft of sensitive personal and organizational information, coupled with extortion demands that sent shockwaves far beyond the racing community.
For small and medium-sized businesses (SMBs) in North Carolina, this case is more than a headline. It is a direct warning. Cyberattacks no longer target just large corporations; criminals go after anyone vulnerable, and SMBs are often easier prey.
In this comprehensive blog, we’ll explore:
- What exactly happened in the NASCAR data breach.
- Who is behind the Medusa ransomware attack.
- Why this event matters deeply for businesses of all sizes.
- What SMBs in North Carolina can do to protect themselves.
The NASCAR Data Breach – What Really Happened
Timeline of the Incident
NASCAR reported that it experienced unauthorized access to its systems between March 31 and April 3, 2025. On April 3, the organization detected unusual activity and quickly launched an investigation. By partnering with external cybersecurity experts and notifying law enforcement, NASCAR began to piece together the full scope of the incident.
By late June, the investigation confirmed the breach involved theft of sensitive personal data. On July 24, 2025, NASCAR began notifying individuals whose information was exposed. The notifications revealed that stolen data included names, addresses, and Social Security numbers, along with other potentially sensitive identifiers.
What Information Was Stolen
The Medusa ransomware gang claimed to have stolen over 1 terabyte of data. Some of the exposed files included:
- Internal raceway maps and event planning documents.
- Employee job titles, email addresses, and HR data.
- Sponsorship contracts and financial invoices.
- Strategic corporate documents and reports.
This wasn’t just about encrypted files. This was a classic double-extortion scheme—attackers not only locked systems but also threatened to leak data unless their demands were met.
The Ransom Demand
Medusa posted NASCAR on its dark-web leak site, demanding a staggering $4 million ransom. To pressure NASCAR, the group threatened to leak sensitive files publicly. Reports suggest they even offered a one-day deadline extension for an extra $100,000, turning the situation into a ticking time bomb.
It is unclear whether NASCAR paid the ransom, but as of this writing, no major public data dump has surfaced. Still, the incident highlights just how ruthless ransomware operators can be.
Understanding Medusa Ransomware
Who is Medusa?
First spotted in 2021, the Medusa ransomware group has grown into one of the most dangerous players in the cybercrime landscape. Operating under the Ransomware-as-a-Service (RaaS) model, Medusa rents its malicious tools to affiliates who carry out attacks. In exchange, Medusa takes a share of the ransom.
Medusa is notorious for targeting sectors ranging from healthcare and education to legal services and government agencies. In March 2025, a joint advisory from the FBI and CISA warned that Medusa was behind over 300 documented attacks, crippling critical services worldwide.
The Double-Extortion Playbook
Medusa’s typical approach includes:
- Infiltration: Gaining access through phishing emails, weak credentials, or exploited vulnerabilities.
- Data Theft: Exfiltrating sensitive information before deploying ransomware.
- Encryption: Locking down critical files and systems.
- Extortion: Demanding payment under threat of leaking stolen data.
This “double hit” means even businesses with good backups may still face blackmail if stolen data includes personal or regulated information.
Medusa’s Evolving Tactics
Security experts note that Medusa increasingly uses “living off the land” techniques—leveraging legitimate tools like PowerShell or stolen certificates to hide in plain sight. This makes detection harder, even for businesses with monitoring tools in place.
Why the NASCAR Breach Matters for North Carolina SMBs
You may be thinking: “I don’t run a billion-dollar sports franchise. Why should I worry about this?”
Here’s why:
- Attackers Don’t Care About Size
Cybercriminals often target SMBs precisely because they assume smaller firms lack robust defenses. A law office in Raleigh or a manufacturing shop in Durham may seem less glamorous than NASCAR, but to hackers, data is data. - Regulatory & Legal Exposure
NASCAR had to report to Attorneys General across multiple states. If your business stores sensitive customer data—like Social Security numbers or health records—you’re subject to similar breach notification laws. Noncompliance can result in fines and lawsuits. - Trust and Reputation
Once customers learn their personal data has been exposed, rebuilding trust is hard. NASCAR has a global brand to lean on, but a small local business could be devastated. - Operational Downtime
Imagine if ransomware locked your QuickBooks files, point-of-sale system, or customer management database. For SMBs, even a few days offline can cause irreparable financial damage.
Lessons Learned from NASCAR’s Cyber Breach
The NASCAR case highlights several critical takeaways:
- Data Breaches Are Multi-Faceted: It wasn’t just IT disruption—it also threatened financial, legal, and reputational damage.
- Speed of Response Matters: NASCAR’s quick engagement of cybersecurity experts and law enforcement demonstrates the importance of having an incident response plan.
- Transparency Is Required: NASCAR had no choice but to notify individuals and regulators—something all SMBs must prepare for under state and federal laws.
Cybersecurity in the Fast Lane – Practical Steps for SMBs
If you own a small or medium business in North Carolina, here’s how to avoid becoming the next headline:
- Run a Cybersecurity Audit
Understand your vulnerabilities. Just as NASCAR inspects every part of its cars before a race, you must inspect your IT systems for weak points.
- Implement Multi-Factor Authentication (MFA)
Stolen passwords remain the number one entry point for ransomware attacks. MFA adds an essential extra barrier.
- Practice Least Privilege Access
Not every employee needs access to sensitive files. Limit permissions to reduce insider threats.
- Backups—But Smarter
Backups are critical, but remember, Medusa’s double-extortion tactics mean backups alone won’t save you. Encrypt backups, store them off-site, and test recovery regularly.
- Monitor for Suspicious Behavior
Invest in logging and monitoring tools. Unusual activity—like bulk file downloads—should trigger alerts.
- Employee Awareness Training
Phishing remains the number one attack vector. Regular training ensures employees can spot suspicious emails.
- Incident Response Plan
Know who to call, what to shut down, and how to communicate with customers and regulators in case of an attack.
- Consider Cyber Insurance
Policies can cover ransom payments, legal fees, and recovery costs. Just make sure coverage extends to extortion and breach notifications.
Analogy – Cybersecurity as a NASCAR Pit Crew
Think of your business as a race car on the track. The car itself—your products, services, and operations—needs to run smoothly. But without a strong pit crew—your IT and security team—you’re vulnerable to breakdowns mid-race.
NASCAR invests in both the car and the crew. Similarly, SMBs must invest in both technology and processes to ensure they can keep racing ahead, even when unexpected obstacles arise.
Looking Ahead – The Future of Cybersecurity for Businesses
The NASCAR incident is just one example in a growing trend. Cybercriminal groups are becoming more professionalized, using RaaS models and collaborating globally.
For SMBs in North Carolina, the future will require:
- Proactive investment in cyber security (not reactive patching after an incident).
- Compliance with evolving regulations, including state-level breach notification laws.
- Continuous employee education, since human error remains the weakest link.
- Partnerships with IT service providers, who bring expertise without the cost of an in-house department.
Conclusion
The NASCAR data breach via Medusa ransomware is more than just a headline from the racing world—it is a cautionary tale for every business in North Carolina. It proves that no brand is too big to fall and no business is too small to be targeted.
As a business owner, the choice is clear: treat cybersecurity as an essential investment, not an afterthought. Just as NASCAR relies on speed, precision, and preparation to win races, your company must rely on vigilance, planning, and strong defenses to survive the cyber threat landscape.
In cybersecurity, as in racing, the winners are those who anticipate challenges, prepare ahead of time, and never take their eyes off the track.

