Microsoft Under Fire for Encryption Weaknesses: What It Means for North Carolina Businesses
Why North Carolina Needs to Pay Attention
While Microsoft’s encryption weaknesses and security failures are a national concern, they carry unique risks for North Carolina organizations. The state is home to a diverse mix of industries — from healthcare (Duke Health, UNC Health, WakeMed), to finance (Bank of America’s Charlotte HQ, regional credit unions), to universities (NC State, UNC Chapel Hill, Duke) — all of which rely heavily on Microsoft environments.
A single unpatched vulnerability or weak encryption setting can expose protected health information (PHI), student records, or financial data, leading to breaches that trigger not only federal penalties (like HIPAA or FTC actions) but also North Carolina’s own stringent data breach notification laws.
State Regulations and Compliance Landscape
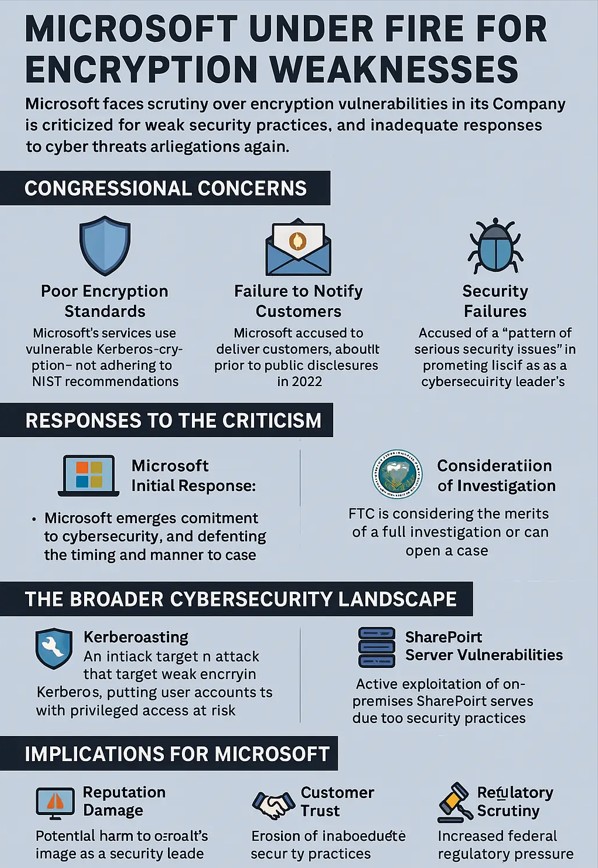
- North Carolina Identity Theft Protection Act (NCITPA)
- Requires businesses and government agencies to implement reasonable security measures to protect personal information.
- If RC4-enabled Kerberoasting or an unpatched SharePoint server leads to a breach, failure to adopt “reasonable” encryption standards could be interpreted as negligence under this law.
- Organizations must notify affected NC residents “without unreasonable delay” after a breach.
- HIPAA & Healthcare in NC
- North Carolina is a major healthcare hub, and healthcare providers are already under HIPAA Security Rule obligations to implement “addressable” encryption controls.
- Hospitals in Charlotte, Raleigh, and Durham running unpatched Microsoft systems risk not just operational downtime but HIPAA fines and loss of trust.
- North Carolina Department of Information Technology (NCDIT) Cybersecurity Guidelines
- NCDIT enforces state-level IT security requirements for agencies and contractors.
- These guidelines align with NIST standards and explicitly recommend strong encryption and regular patching. Continuing to rely on RC4 or ignoring Microsoft patch advisories could place state agencies in non-compliance.
- Education Sector Obligations
- Universities in North Carolina handle sensitive student data protected under FERPA. Weak Microsoft security practices could jeopardize compliance and expose universities to lawsuits from students or parents in the event of a breach.
Real-World Example: A North Carolina Case Study
Consider a mid-sized law firm in Raleigh that handles sensitive client financial records.
- They use Microsoft Active Directory for authentication and SharePoint for case collaboration.
- Because of legacy software, RC4 remains enabled. A cybercriminal exploits Kerberoasting to extract service account hashes, cracking passwords in hours.
- The attacker gains access to privileged accounts, stealing case files and banking details.
Consequences for the firm:
- Under NCITPA, the firm must notify all affected NC residents.
- The NC Attorney General could investigate, citing failure to follow “reasonable security practices.”
- Clients lose trust and switch firms, damaging reputation permanently.
This example underscores how encryption weaknesses are not abstract flaws — they can directly trigger regulatory exposure and business risk in North Carolina.
What NC Businesses Should Do Now
- Assess Legal Exposure Under NCITPA
- Review whether encryption methods in your Microsoft systems qualify as “reasonable security measures.”
- If RC4 is still in use, it’s difficult to argue compliance.
- Patch to Stay Ahead of Regulators
- Apply Microsoft’s SharePoint patches immediately.
- Document patch dates and mitigation efforts for compliance evidence.
- Engage with NCDIT & CISA Alerts
- Subscribe to NCDIT and CISA advisories for guidance specific to state agencies and critical infrastructure.
- North Carolina utilities, municipalities, and public agencies are common Microsoft customers — they must stay aligned with federal and state security alerts.
- Prepare for Incident Response Under NC Law
- Breach notifications in NC are mandatory. Develop a communications plan for rapid compliance.
- Keep your cyber liability insurance provider informed of your encryption and patching practices — insurers are tightening requirements after widespread ransomware attacks.
Local Industry Spotlight
- Healthcare (Triangle region): Hospitals using legacy Microsoft systems should urgently test for RC4, as patient data exposure could combine HIPAA and NC state penalties.
- Financial Services (Charlotte): Banks and credit unions must maintain customer trust. Even a minor breach tied to Microsoft misconfiguration could invite regulatory scrutiny from both federal and NC regulators.
- Education (Chapel Hill, Durham, Raleigh): Universities must patch SharePoint servers or risk FERPA non-compliance. A breach here could also spark student lawsuits, which NC courts increasingly see.
- Municipal Governments: Towns and counties across NC often use Microsoft products for budgeting and citizen services. If breached, not only are services disrupted, but local officials may face accountability for failing to heed warnings.
North Carolina’s Path Forward
North Carolina has positioned itself as a leader in cybersecurity policy and workforce development. With the NC Cybersecurity Strategic Plan and partnerships between state government, universities, and private sector, there’s a growing recognition that:
- Encryption weaknesses cannot be ignored.
- Vendors like Microsoft will be held accountable, but local responsibility remains critical.
- Proactive compliance with NCITPA, HIPAA, FERPA, and NCDIT guidelines is no longer optional — it’s a business survival strategy.
Microsoft’s Weaknesses, NC’s Responsibility
Microsoft is rightly under fire for encryption weaknesses and slow response to vulnerabilities. But while regulators may investigate, organizations in North Carolina cannot afford to wait.
- Healthcare providers in Durham, banks in Charlotte, law firms in Raleigh, and schools across the state must act now — audit encryption settings, patch quickly, and align with state and federal laws.
- Breaches in North Carolina have a double cost: legal penalties and community trust.
- Cybersecurity is not just Microsoft’s responsibility; it’s a shared obligation.
For North Carolina organizations, the lesson is clear: treat Microsoft’s weaknesses as your call to strengthen your defenses now.

